Internet, E Mail and
Electronic Communication Policy
Order Policy Download Table of Contents
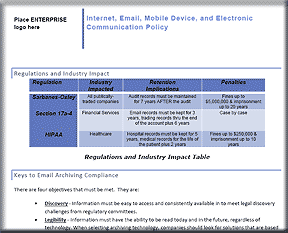
This policy is twenty-three (23) page in length, is compliant with all recent legislation (SOX, HIPAA, Patriot Act, and Sensitive information), and covers:
- Appropriate use of equipment
- Internet access
- Electronic Mail
- Retention of e-mail on personal systems
- E-mail and business records retention
- Copyrighted materials
- Banned activities
- Ownership of information
- Security
- Sarbanes-Oxley
- Abuse
Included with the policy are forms that can be used to facilitate the implementation of the policy. Included are these ready to use forms:
- Internet & Electronic Communication Employee Acknowledgement (short form)
- E-Mail - Employee Acknowledgement (short form)
- Internet Use Approval Form
- Internet Access Request Form
- Security Access Application Form
Order Policy Download Table of Contents
The WORD template uses the latest CSS style sheet and can easily be modified to conform to the style used in your enterprise policy manual.